IKEv2 configuration guide for all major platforms
IKEv2 proves itself to be extremely secure while also demonstrating high stability and performance speed. Therefore, it will be no wonder if you decide to use it on your device. This guide will walk you through the IKEv2 setup on the most popular platforms, such as iOS, macOS, and Windows. So let's start!
First of all, you need to create manual configuration files. In this regard, please follow a few simple steps described in our tutorial.
Please note that this option is considered equivalent to 1 active device, therefore occupies 1 slot.
Now, choose your platform and follow a few simple steps.
1. First, you have to install the security certificate provided by VPN Unlimited.
Double-click the certificate file (.crt) and select Open for the security request.
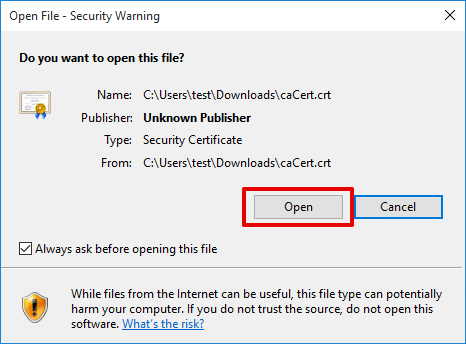
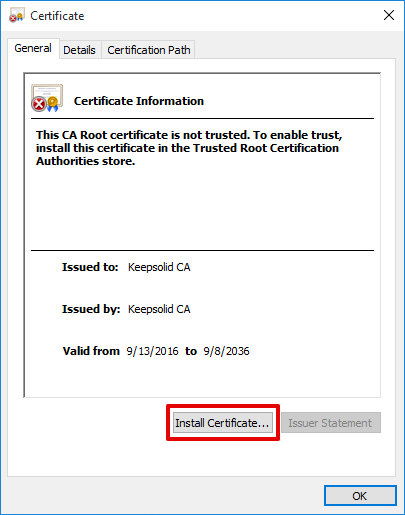
2. Click Install Certificate.
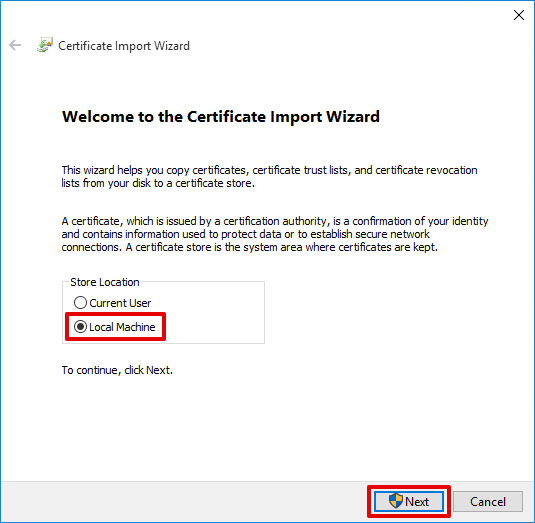
3. Select Local Machine for the Store Location and click Next.
4. Press Yes for the User Account Control request.
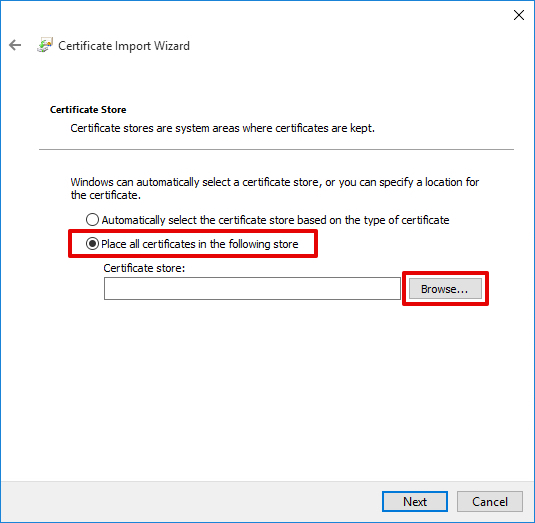
5. Choose the Place all certificates in the following store option and click Browse.
6. Select Trusted Root Certification Authorities. Click OK and then Next.
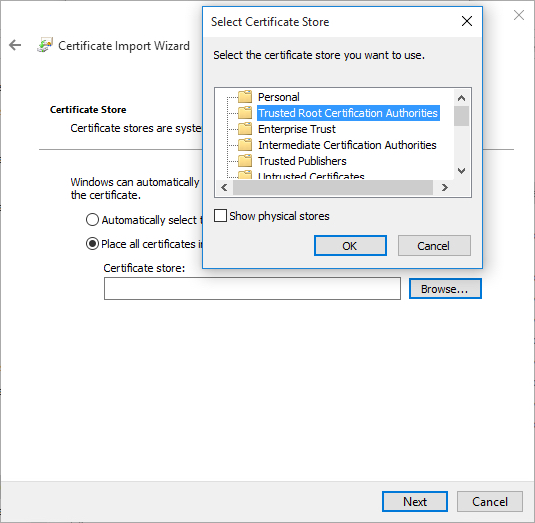
7. In the next window, click Finish.
8. Now, when the certificate is successfully installed, it's time to configure a VPN connection.
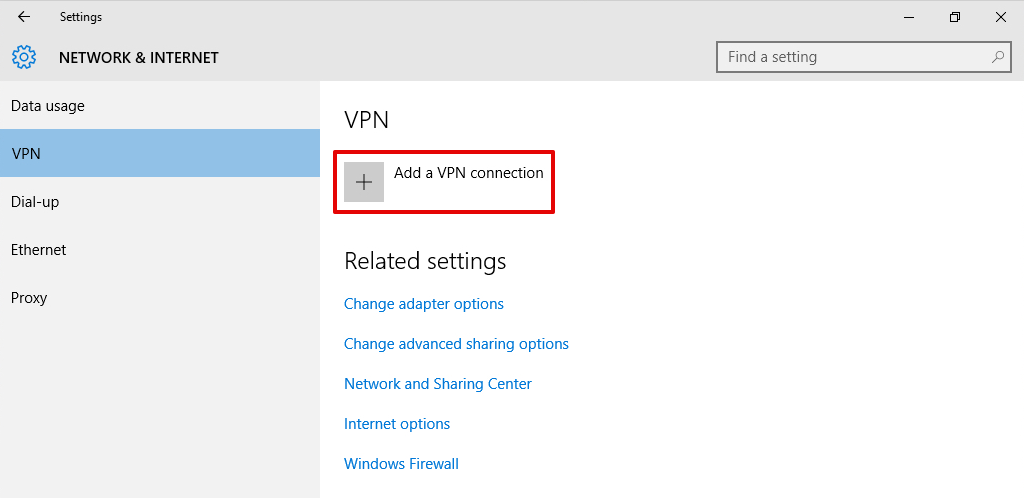
Navigate to Settings > Network & Internet > VPN and click Add a VPN connection.
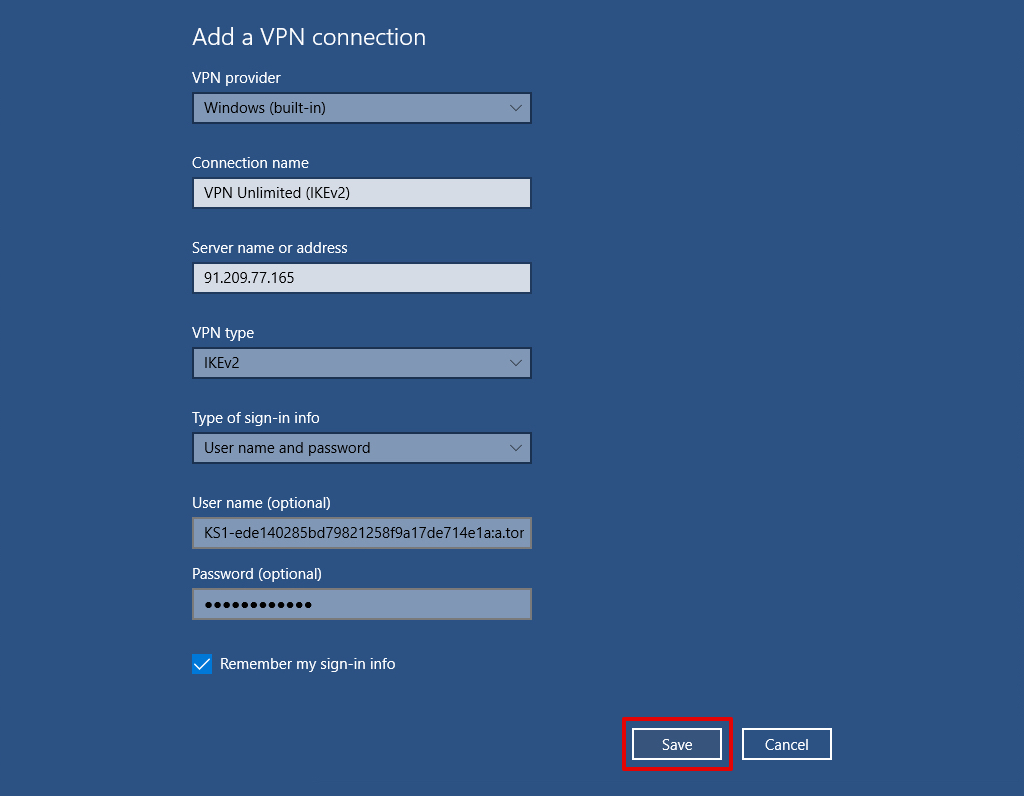
9. Input the following data:
VPN provider: Windows (built-in)
Connection name: Enter any name of your choice, for instance, VPN Unlimited (IKEv2)
Server name or address: Enter the IP address of the desired server provided by VPN Unlimited
VPN type: IKEv2
Type of sign-in info: User name and password
User name: Enter the user name provided by VPN Unlimited
Password: Enter the password provided by VPN Unlimited
When you finish, click Save.
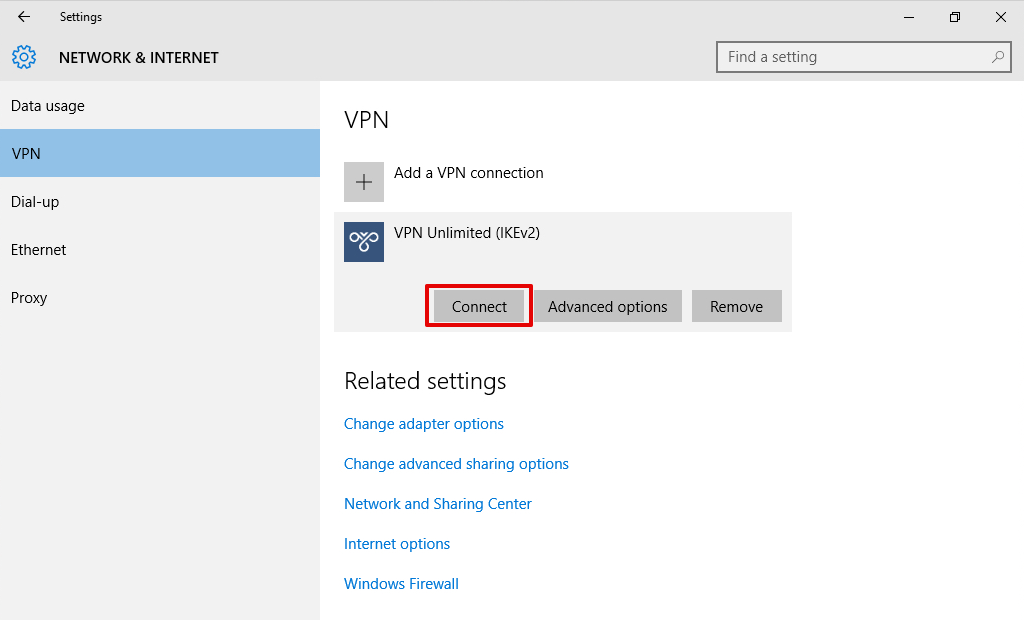
10. Click Connect and the VPN connection will be established in few seconds.
That's about it. Now you have a running VPN connection through the IKEv2 protocol.
Important! Please note that you will need to configure your device using the generated settings by yourself at your own risk.

